HTTPS
# HTTPS
HTTP + S ==> HyperText Transfer Protocol + Secure
HTTPS extends HTTP and uses encryption for secure communications between client and server.
# Why use HTTPS
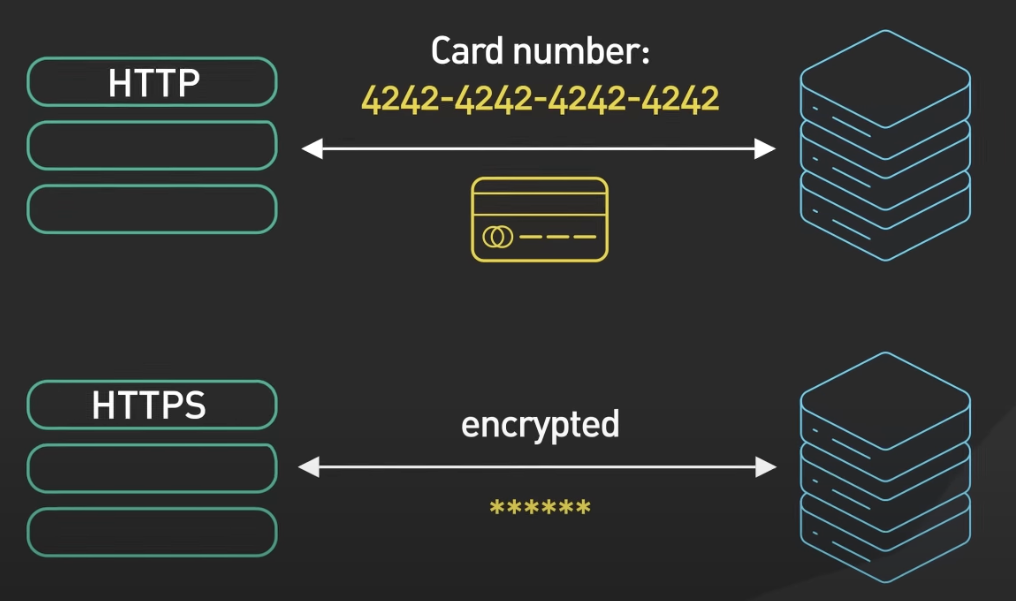
With HTTP, the communication between the browser and the server is in plain text, this means that the password you enter or credit card number you send over the internet can be read by anyone who can intercept it.
HTTPS is designed to solve this problem by making the data sent over the Internet unreadable by anyone other than the sender and the receiver.
# Step-by-step breakdown
Here's a step-by-step breakdown of how HTTPS works in client-server communication:
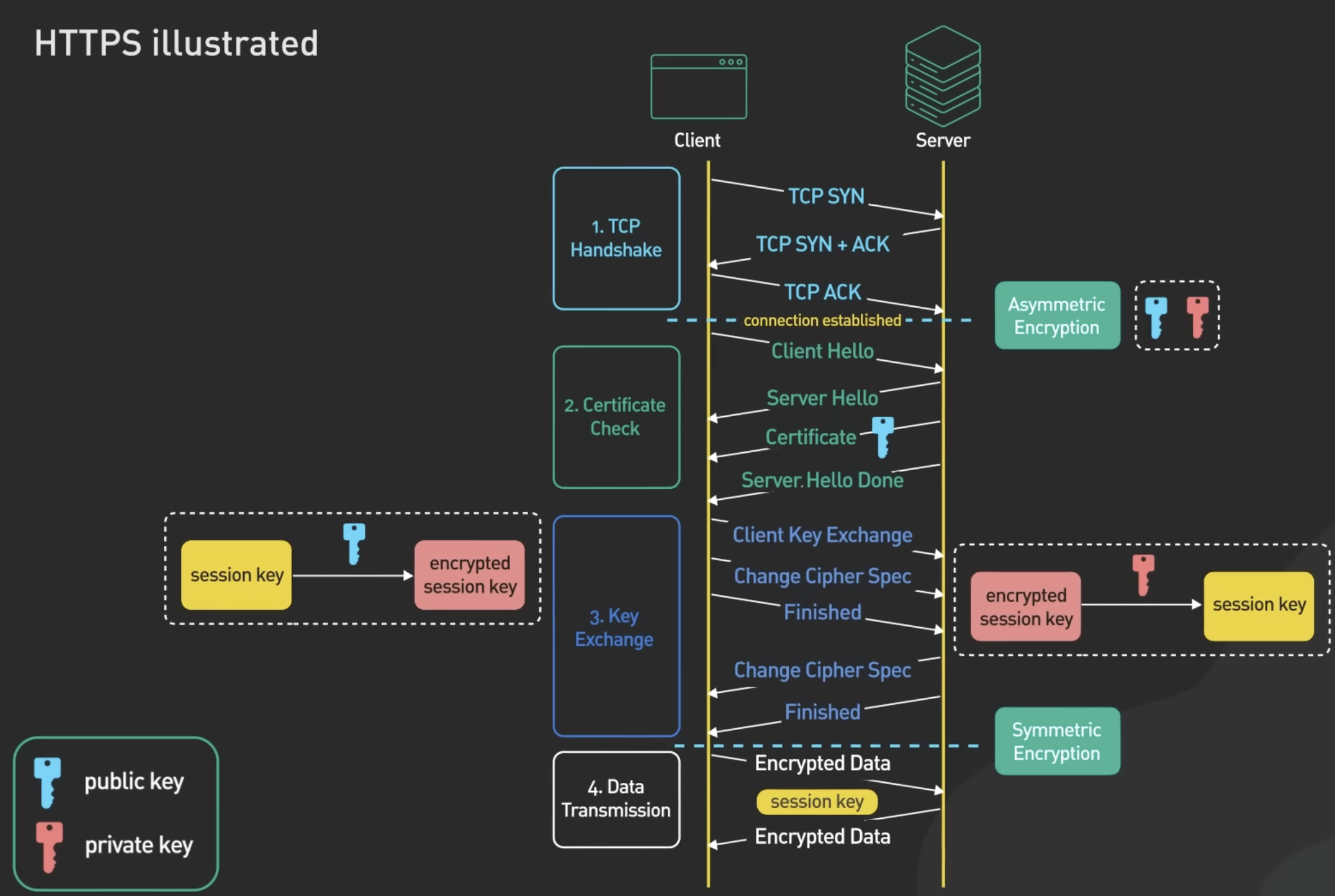
# TCP handshake
Step 1: Client Initiates a Connection
- The client (usually a web browser) initiates a TCP connection with the server.
# Certificate check
Step 2: Server Sends the Certificate
- The browser sends a "Client Hello" message to the server, informing what TLS version and cipher suites it supports (1.2, 1.3, etc).
Format of "Client Hello" and "Server Hello":- Version: highest version of TLS/SSL client supports
- Random number: 256 bits
- Session ID: identify session key
- Cipher suites
- Extensions
- The server sends a "Server Hello" message to the client, specifying the TLS version and cipher suites it's going to use based on options given by client.
- The server then sends its digital certificate, which includes the server's public key and other metadata.
- The certificate is typically signed by a trusted Certificate Authority (CA), confirming its legitimacy.
- The server sends a "Server Hello Done" message with empty body to indicate that the server has nothing more to send at this time.
Step 3: Client Verifies the Certificate
- The client checks the certificate to ensure it's signed by a trusted CA.
- It also checks for other indicators of trustworthiness, such as the certificate's expiration date.
# Key exchange
Step 4: Client Generates a Pre-Master Secret
- If the certificate is valid, the client generates a pre-master secret, a random number for this session.
- 2 bytes: TLS / SSL version
- 46 bytes: random
Step 5: Client Encrypts Pre-Master Secret with Server's Public Key
- The client encrypts the pre-master secret using the server's public key obtained from the digital certificate.
Step 6: Server Decrypts to Obtain Pre-Master Secret
- The server receives the encrypted pre-master secret and decrypts it using the matching private key, which only the server knows.
Step 7: Both Generate Symmetric Session Key
- Both the client and server use the pre-master secret to generate the same symmetric session key.
- Pre-master secret is used to derive master secret.
- Then master secret is used to generate session keys.
- This session key will be used to encrypt and decrypt all subsequent communication in this session.
Step 8: Client Sends Acknowledgment
- The client sends a message encrypted with the session key to indicate it's ready to begin encrypted communication.
Step 9: Server Sends Acknowledgment
- The server decrypts the client's message using the session key to verify that they're both using the same key.
- The server then sends its own acknowledgment, also encrypted with the session key.
# Data transmission
Step 10: Secure Communication
- At this point, the handshake is complete, and both the client and server can communicate securely using the session key to encrypt and decrypt messages.
Step 11: Session Termination
- Either the client or server can choose to terminate the session. Upon termination, the session key is discarded.